Avaya Modular Messaging setup
Avaya Modular Messaging is a standards-based messaging system that
runs on the S3400 Message Server system. Avaya Modular Messaging
converges voice and data networks and is a critical system for messaging
and communications. Based on the functions, it is divided into two
separate components:
Messaging Application Server (MAS). MAS is a Windows-based
system that forms a front end that interfaces with the Private Branch
Exchange (PBX) through associated voice ports.
Message Storage Server (MSS). MSS is a Linux-based
system that forms the back end which provides message storage, message
transport, and directory functions.
One or more MAS with one MSS together form a voice mail domain.
The MAS and the MSS communicate over a dedicated private LAN. The
MAS and the MSS together provide callers with a call-answering interface,
subscribers with access to messages and directory, and administrators
with access to system and subscriber configuration data. With this
setup, Avaya has implemented various features and recommendations
to provide users with a secure system that easily fits into their
existing security profile.
Figure 1. Modular Messaging System
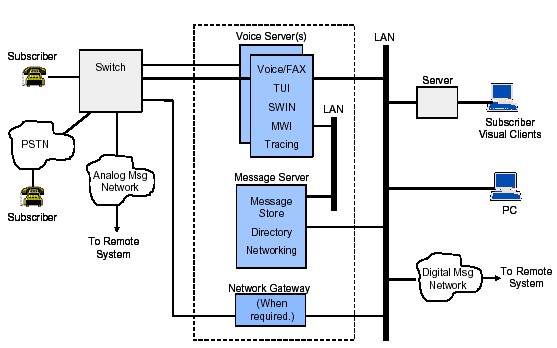 |
Security elements with Modular Messaging
Security concerns for the Avaya S3400 Message Server include toll
fraud, unauthorized reprogramming of computer systems, unauthorized
access to telecommunication system by misusing the call transfer
capabilities of the system or through ports meant for remote
administration or maintenance, unintended disclosure of confidential
information, and virus attacks. These activities result in huge
telephone bills, revenue loss, administrative costs, decreased system
performance, and loss of customer confidence. The various security
risks faced by telecommunication systems today are described in
the following sections.
Telecommunications Fraud
Toll Fraud is a significant security concern in traditional voice
messaging systems. Unauthorized people use personal computers, random
number generators and password cracking programs to break into the
most sophisticated systems and commit frauds. Today, with the convergence
of voice and data and the advent of IP Telephony, security problems
are not limited to toll fraud and unauthorized access. The advancement
in technology has opened up a wide array of vulnerabilities that
can compromise the security of the entire organization. See Telecommunication
service thefts for more information on Toll Fraud.
Voice messaging features
Voice messaging systems provide a wide variety of applications,
such as automated attendants, that operate like an electronic answering
machine. Callers can leave messages for employees who have voice
mailboxes assigned to them. These features allow the transfer of
calls out of the voice mailboxes and into the PBX system. Hackers
try to connect to the voice mail system and type-in digits to gain
an outgoing trunk line. Some hackers gain entry into the voice messaging
system and search for unassigned mailboxes. They then use such mailboxes
to exchange toll-free messages. In addition, unauthorized access
to the voice mail system also allows hackers to gain access to PBX
and manipulate the administrative data.
Remote access
Remote access (also known as DISA, Direct Inward System Access)
permits callers to access the system from public networks. Callers
can dial into the system using CO, FX, DID or 800 service trunks
to use the features and services of the system. Unprotected remote
access numbers are a favorite target for hackers. Hackers attempt
to decipher the security code by using automated programs to gain
entry into the system and misuse its services. Expert toll hackers
also target the administration and maintenance ports of systems
to change the system features and parameters to make unauthorized
long distance calls.
Internal threats
Securing a system does not begin with the system itself, but with
the people and organizations that use it. In deciding who to protect
the system against, one must not forget to look internally. A significant
number of attacks come from within. Internal security is important
to the protection of information and assets. It is easier to misuse
or damage the system by physical methods than by hacking the system
passwords. Employees can easily access the mailbox of another employee
and pass critical and confidential information, such as passwords,
to unauthorized people. It is necessary to enforce a proper security
policy against such internal breach of communications.
Internet threats
Modular Messaging is deployed into the existing corporate LAN and
is exposed to the Internet. Security is a primary concern when an
organization connects its network to the Internet. Network administrators
have increasing concerns about the security of their networks when
they expose their organization’s private data and networking
infrastructure to Internet crackers. Some of the common methods
of attacks from the Internet include Internet worms, virus attacks,
malicious e-mail attachments, IP spoofing, Password attacks, Network
packet sniffers, Denial of Service attacks, and Application layer
attacks. These attacks can lead to theft, and to destruction and
corruption that can cause irreparable damage to sensitive and confidential
information.
What you need to do
It is extremely important that system managers and administrators
plan and implement the necessary security measures and ensure that:
-
Modular Messaging servers integrate into your existing TCP/IP
network in accordance with the corporate networking policies,
and these servers also allow the usage of existing firewall
and of corporate security policies and practices.
-
The network prevents exposure of potentially sensitive customer
messages by using sending restrictions that provide data for
you to check to ensure that there has been no unauthorized usage.
-
You prevent unauthorized use of the server capabilities by
protecting the server with administrator and user passwords.
Lengthy and random passwords minimize the possibility of hacking.
-
The network prevents unauthorized command-line access to the
main server.
-
The network prevents all well known types of hacker attacks,
including denial of service attacks.
-
The servers provide sufficient logs, like the Administrator
History Log, to facilitate detection of actual and attempted
unauthorized usage and identification of sources of unauthorized
usage.
Top of page
|

