| |
Security of Your System. As a customer of a new communications system,
you should be aware that telephone toll fraud is an increasing problem.
Telephone toll fraud can occur in many forms, despite the numerous efforts
of telephone companies and telephone equipment manufacturers to control
it. Some individuals use electronic devices to prevent or falsify records
of these calls. Others charge calls to someone else's number by illegally
using lost or stolen calling cards, billing innocent parties, clipping
on to someone else's line, and breaking into someone else's telephone
equipment physically or electronically. In certain instances, unauthorized
individuals make connections to the telephone network through the use
of Remote Access features.
The Remote Access feature of your system, if you choose to use it, permits
off-premises callers to access the system from a remote telephone by using
an 800 number or a 7- or 10-digit telephone number. The system returns
an acknowledgment signaling you to key in your barrier code, which is
selected and programmed by the System Manager. After the barrier code
is accepted, the system returns a dial tone to you. If restrictions are
not in place, you can place any call normally dialed from a telephone
within the system. Such an off-premises network call is originated at,
and will be billed from, the system location.
The Remote Access feature, as designed, helps the customer, through proper
programming, to minimize the ability of unauthorized persons to gain access
to the network. Most commonly, telephone numbers and codes are compromised
when overheard in a public location, through theft of a wallet or purse
containing access information, or through carelessness (writing codes
on a piece of paper and improperly discarding it). Additionally, hackers
may use a computer to dial an access code and then publish the information
to other hackers. Enormous charges can be run up quickly. It is the customer's
responsibility to take the appropriate steps to properly implement the
features, evaluate and program the various restriction levels, protect
access codes, and distribute access codes only to individuals who have
been fully advised of the sensitive nature of the access information.
Common carriers are required by law to collect their tariffed charges.
If these charges are fraudulent charges made by persons with criminal
intent, applicable tariffs state that the customer of record is responsible
for payment of all long-distance or other network charges. Lucent Technologies
cannot be responsible for such charges and will not make any allowance
or give any credit for charges that result from unauthorized access.
To minimize the risk of unauthorized access to your communications system:
- Program the maximum length (11) for system-wide barrier code length.
- Use an unpublished Remote Access number.
- Assign barrier codes randomly to users on a need-to-have basis, keeping
a log of all authorized users and assigning one code to one person.
- Use random-sequence barrier codes, which are less likely to be easily
broken.
- Deactivate all unassigned codes promptly.
- Ensure that Remote Access users are aware of their responsibility
to keep the telephone number and any barrier codes secure.
- When possible, restrict the off-network capability of off-premises
callers, through use of calling restrictions and Disallowed List features.
- When possible, block out-of-hours calling.
- Frequently monitor system call detail reports for quicker detection
of any unauthorized or abnormal calling patterns.
- Limit Remote Call Forwarding to persons on a need-to-have basis.
- Change barrier codes periodically.
- Additional security to prevent telephone toll fraud is included:
- The Remote Access default requires a barrier code.
- The barrier code is a flexible-length code ranging from 4 to 11 digits
(with a default of 7) and includes the * character. The length is set
system-wide.
- The user is given three attempts to enter the correct barrier code.
- Whether or not the dialed digits are correct, an inter-digit time-out
occurs during the first attempt. The system processes only the valid
number of digits. So if a hacker enters four digits and the length is
four digits, he or she hears dial tone. If a hacker enters four digits
and keeps entering more, the system uses the time-out to hide the correct
number of digits from the hacker. The time-out recurs until the caller
has dialed the eleventh digit--giving the impression that additional
digits are required--even if the barrier code length is shorter.
- SMDR registers 16 zeros for any Remote Access calls in which three
failed attempts have occurred.
|
 RemoteAccss
RemoteAccss LinesTrunks
LinesTrunks
 RemoteAccss
RemoteAccss Non-Tie/Tie
Lines
Non-Tie/Tie
Lines Restriction/ARS
Restrct/AllowList/DisallowList
Restriction/ARS
Restrct/AllowList/DisallowList  RemoteAccss
RemoteAccss BarrierCode
Restriction/ARS Restrct/AllowList/DisallowList
BarrierCode
Restriction/ARS Restrct/AllowList/DisallowList  RemoteAccss
RemoteAccss Non-Tie/Tie
Lines
Non-Tie/Tie
Lines BarrierCode
BarrierCode
 RemoteAccss
RemoteAccss BarrierCode
BarrierCode CodeInfo
CodeInfo
 RemoteAccss
RemoteAccss BarrierCode
BarrierCode SProgMaint
SProgMaint
 RemoteAccss
RemoteAccss AutoQueuing
AutoQueuing

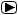 or More
or More Unassigned
Unassigned
 Single
Single RemoteAccs
RemoteAccs
