Bash Vulnerability
Collapse
X
-
Shellshock/Bash impact update for Avaya products
Avaya’s Product Security Team is aware of the Shellshock security issue and is working aggressively with product teams across our portfolio to assess any possible impact and identify a mitigation plan as appropriate. An Avaya Security Advisory (ASA) will be published later today, Friday 26 September at approximately 7pm ET. The Product Security team will continue to report findings as they become available.
Please visit the following link on the Avaya Support Website for the latest information on this topic. All ASAs for Shellshock will be posted to this site.
Avaya Support Website – Shellshock/Bash Impact for Avaya Products - https://support.avaya.com/helpcenter...26131554370002Russ Brookes | Avaya, KCS Leader | +1 613.771.7590 | [email protected] | NA Eastern Time Zone
Comment
-
-
hi
are avaya telling the customers to wait until they have included updates in patchs / security updates or are avaya telling customers to go ahead and use the updates from the RedHat site ?
I have read the bulletin from Avaya but it is not clear to me what is the recommended course of action ?
Thanks
Darren
Comment
-
-
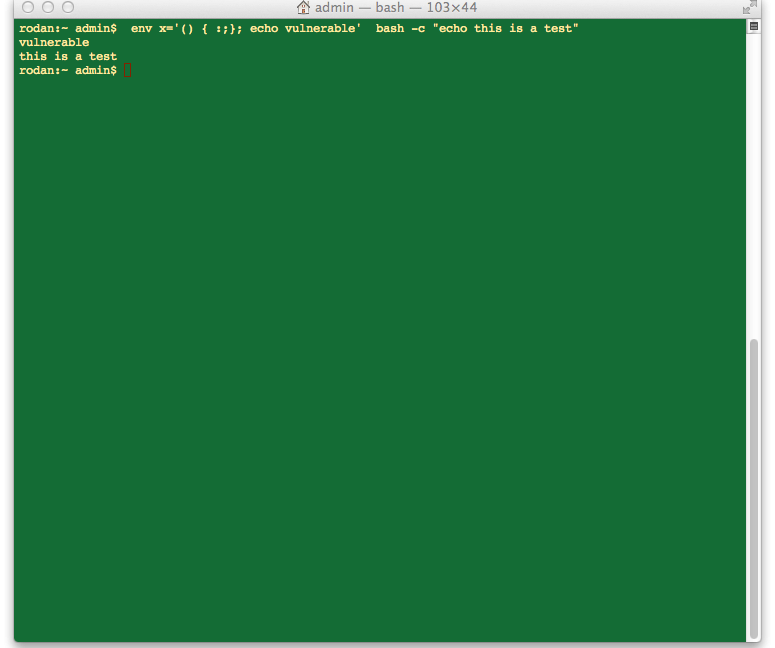
Originally posted by richa164 View PostRun this test from linux shell.
env x='() { :;}; echo vulnerable' bash -c "echo this is a test"
If you get
Vulnerable
This is a test
Well guess what !!
and now just checking my LAB's
Here is the result for the Communication Manager
dadmin@CM-LAB> env x='() { :;}; echo vulnerable' bash -c "echo this is a test"
vulnerable
this is a test
Result for my DOM0
[admin@CM2-SPDom0 ~]$ env x='() { :;}; echo vulnerable' bash -c "echo this is a test"
vulnerable
this is a test
[admin@CM2-SPDom0 ~]$
Result for my CDOM0
[admin@CM2-SPCdom ~]$ env x='() { :;}; echo vulnerable' bash -c "echo this is a test"
vulnerable
this is a test
[admin@CM2-SPCdom ~]$
So that mean i am Vulnerable.
is there an offcial procedure from Avaya to find out.
DanielLast edited by audetd; 10-02-2014, 12:27 PM._____________________________
Daniel
Allstream Application Specialist
Comment
-
-
I have installed the 6.2 patch in my Lab and the script test does not show the Vulnerable word any more.
But Platform still show it. so we will need patch later on this one.
Here is the link where i got the patch.
Last edited by audetd; 10-02-2014, 04:37 PM._____________________________
Daniel
Allstream Application Specialist
Comment
-
-
I have install on CM 6.2 Via Platform and this is HOT not service affectingOriginally posted by jaytarbox View PostPatches out for various CM versions now, no indication if they're service interrupting or not.
See my screen capture in attachement_____________________________
Daniel
Allstream Application Specialist
Comment
-





 .
. .
.

Comment