NOTE: As with any process such as this, we advise that a backup be taken prior to beginning.
First off, it is important to decide what information is needed when creating your new root CA.
There is a utility which is included in release SMGR 6.3.9 onwards called createCA.bin which allows you to create a root CA quickly and easily in a 1 step process. However, you are limited to only being able to provide a Common Name (CN) value for the new root CA.
If this is ok, then please refer to the Administering System Manager guide for details on how to run the createCA.bin script and ignore the following steps.
However, if you want to have more control over the values of your new root CA such as providing more information in the subject DN than just the CN or configuring the Signing Algorithm, etc then please follow the steps below to manually create your new root CA.
NOTE: As with any process such as this, we advise that a backup be taken prior to beginning
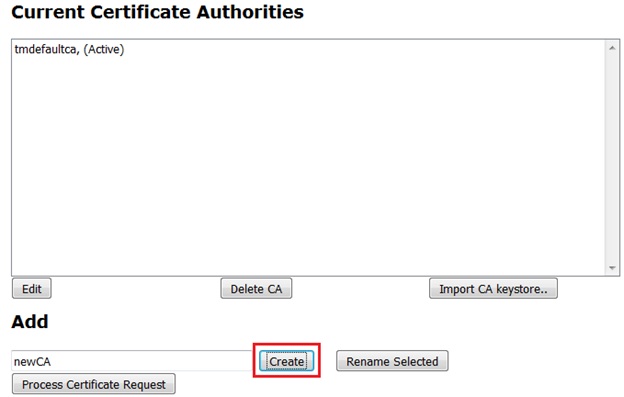
First of all you need to define the new CA. To do this, log into the SMGR web interface, navigate to Security->Certificates->Authority and click on the Edit Certificate Authorities menu on the left
Enter a temporary name for your new CA and click on the Create button
You will then see a screen where the components of the new CA can be configured.
Adjust the settings as necessary for example:
| Signing Algorithm |
SHA256WithRSA |
| RSA key size |
2048 |
| Subject DN |
CN=Tonys SMGR CA,OU=ETSS,O=AVAYA,L=PONTYPRIDD,ST=CARDIFF,C=GB |
| Validity (Days) |
1825 |
NOTE: Ensure that the Signed By field is set to Self Signed
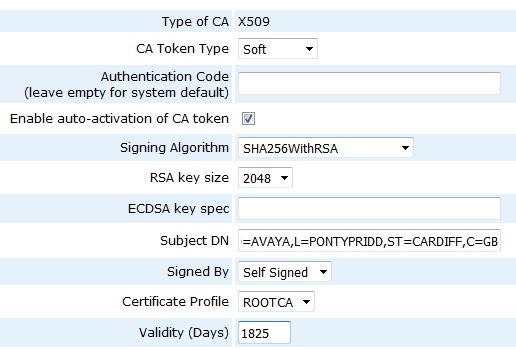
When finished, click on the Create button
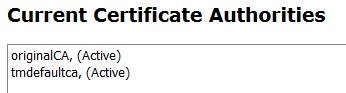
You will then see that there are 2 active CAs. The original (tmdefeaultca) and the new CA (newCA)
In SMGR 6.3, the system is hard coded in certain areas to always use the tmdefaultca CA so we now need to rename the CAs.
To do this, select tmdefaultca from the list box and in the text box below, enter a new name such as originalCA. Click on the Rename Selected button
Then select the new CA from the list box and in the text box below enter the value tmdefaultca and click on the Rename Selected button again
You should now have the same 2 active CAs but the original tmdefaultca is called originalCA and your new CA is called tmdefaultca
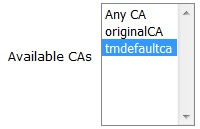
Click on the Edit Certificate Profiles menu on the left
Edit each of the following profiles in turn and ensure that the tmdefaultca CA is selected in the Available CAs list box and then click on the Save button:
ID_CLIENT
ID_CLIENT_SERVER
ID_SERVER
Next, click on the Edit End Entity Profiles menu on the left
Edit each of the following profiles in turn and ensure that the tmdefaultca CA is selected in the Available CAs list box and then click on the Save button:
EXTERNAL_CSR_PROFILE
INBOUND_OUTBOUND_TLS
INBOUND_TLS
OUTBOUND_TLS
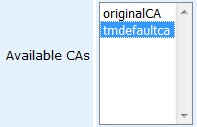
Next, click on the List/Edit End Entities menu on the left
Set the Or with status field to All and click on the List button
This will display a list of all End Entities:
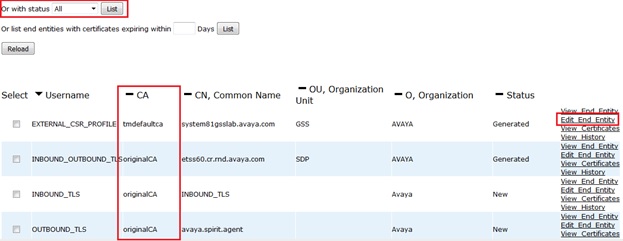
Check the CA column and if it already shows tmdefaultca then you can skip that entity and move on to the next one.
If it doesn’t show tmdefaultca then click on the Edit End Entity link on the right of the Entity and change the CA field to tmdefaultca and then click on the Save button followed by the Close button.
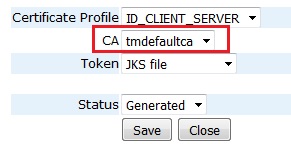
Once all of the Entities have been updated, click on the List button again to refresh the list and now all Entities should show tmdefaultca in the CA column.
Next, navigate on the SMGR dashboard to Inventory->Manage Elements and select the System Manager entry. Click on More Actions->Configure Identity Certificates
You should be presented with a list of certificates. Select the JONA certificate and scroll down to make a note of the Issuer Name of that certificate. It should be the current CA (originalCA).
Now, we need to regenerate all of the certificates using the new CA. To do this, log into the SMGR CLI using SSH and run the following command as the root user, please make sure generate new enrollment password before run folowing script
NOTE: This is one single command that may be shown on multiple lines due to its length
sh /opt/Avaya/Mgmt/6.3.8/trs/trust_initializer_install.sh -RMIPORT 1399 -HTTPSPORT 443 -TMCONFIGLOC /opt/Avaya/JBoss/6.1.0/jboss-as/server/avmgmt/conf/tm/
(If this COmmand failed see below section called #FAILED)
This command should take about a minute to run and once complete you should get a message indicating ‘TM Initialization success’
If you receive a failure response, please try the above command again and if it still fails then do not proceed any further and engage Avaya support for assistance.
If you receive a success response then you should restart the SMGR services to load the new certificates using the command below run as the root user:
service jboss restart
After about 15 minutes, the SMGR web interface should be available again. Log back in and navigate back to Inventory->Manage Elements and select the System Manager. Click on More Actions->Configure Identity Certificates and select the JONA certificate again.
This time the Issuer Name should be your new CA. This will be the same for all of the certificates in the list except for the WebLM Legacy certificate. This is a special certificate that is not issued by the SMGRs CA.
NOTE: It is important to realize that as SMGR is now using certificates that have been issued by your new CA, communication will be broken between SMGR and certificate trusted products such as Session Manager, Presence or EDP. You should now reinitialize trust on those products so that they begin to trust the SMGR again and vice-versa.
#FAILED
[root@SMGR-JLT ~]# sh /opt/Avaya/Mgmt/6.3.8/trs/trust_initializer_install.sh -RMIPORT 1399 -HTTPSPORT 443 -TMCONFIGLOC /opt/Avaya/JBoss/6.1.0/jboss-as/server/avmgmt/conf/tm/
Updating virtual FQDN in CRDJEE_Input.xml successfull
****************************
You are installing on machine :192.A.B.52
****************************
Setting up TM service with config /opt/Avaya/JBoss/6.1.0/jboss-as/server/avmgmt/conf/tm/ and service name container_tls
System property has been set for javax.net.ssl.keyStore with value /opt/Avaya/JBoss/6.1.0/jboss-as/server/avmgmt/conf/tm//keystore/container_tls_keystore.jks
System property has been set for javax.net.ssl.keyStorePassword with value gDKPNF3pxwOk
Setting up TM service with config /opt/Avaya/JBoss/6.1.0/jboss-as/server/avmgmt/conf/tm/ and service name TM_INBOUND_TLS
System property has been set for javax.net.ssl.trustStore with value /opt/Avaya/JBoss/6.1.0/jboss-as/server/avmgmt/conf/tm//truststore/default_truststore.jks
System property has been set for javax.net.ssl.trustStorePassword with value gDKPNF3pxwOk
tmConfigurationLocation in TMCli is /opt/Avaya/JBoss/6.1.0/jboss-as/server/avmgmt/conf/tm/
com.avaya.mgmt.trust.tmclient.TMClientLibException: Unauthorized
at com.avaya.mgmt.trust.tmclient.remote.TMServiceRequestRemoteBase.performOperation(TMServiceRequestRemoteBase.java:173)
at com.avaya.mgmt.trust.tmclient.remote.TMServiceRequestRemoteBase.update(TMServiceRequestRemoteBase.java:237)
at com.avaya.mgmt.trust.tmconsole.utils.InitializeTMCli.initialize(InitializeTMCli.java:397)
at com.avaya.mgmt.trust.tmconsole.utils.InitializeTMCli.main(InitializeTMCli.java:182)
****************************
TM Initialization failed. Unable to contact TM Service.
****************************
Return Code: 1 (TM Initialization failed. Unable to contact TM Service.)
checked logs
1)TM.log
2) $JBOSS_HOME/server/avmgmt/logs/ejbca.log
In /ejbca.log isee below error,
2019-11-18 17:11:14,596 ERROR [org.ejbca.core.model.log.Log4jLogDevice] November 18, 2019 5:11:14 PM GST, CAId : -2041228500, CA, EVENT_ERROR_USERAUTHENTICATION, Administrator : PUBLICWEBUSER, IP Address : 192.A.B.52, User : INBOUND_OUTBOUND_TLS, Certificate : No certificate involved, Comment : Got request for end entity INBOUND_OUTBOUND_TLS with invalid password. Verify the password (expiry date and enrollment count if it exists).
2019-11-18 17:11:14,614 ERROR [org.ejbca.ui.web.protocol.ScepServlet] Authorization denied.
org.ejbca.core.model.ca.AuthLoginException: Got request for end entity INBOUND_OUTBOUND_TLS with invalid password. Verify the password (expiry date and enrollment count if it exists).
at org.ejbca.core.ejb.ca.auth.LocalAuthenticationSessionBean.isSCEPPasswordMatched(LocalAuthenticationSessionBean.java:470)
at org.ejbca.core.ejb.ca.auth.LocalAuthenticationSessionBean.authenticateUser(LocalAuthenticationSessionBean.java:348)
at sun.reflect.GeneratedMethodAccessor2892.invoke(Unknown Source)
at sun.reflect.Del
Before start this activity make sure you set a new enrollment password.
[root@SMGR-JLT log]# sh $MGMT_HOME/trs/trust_initializer_install.sh -RMIPORT 1399 -HTTPSPORT 443 -TMCONFIGLOC $JBOSS_HOME/server/avmgmt/conf/tm/
Updating virtual FQDN in CRDJEE_Input.xml successfull
****************************
You are installing on machine :192.A.B.52
****************************
Setting up TM service with config /opt/Avaya/JBoss/6.1.0/jboss-as/server/avmgmt/conf/tm/ and service name container_tls
System property has been set for javax.net.ssl.keyStore with value /opt/Avaya/JBoss/6.1.0/jboss-as/server/avmgmt/conf/tm//keystore/container_tls_keystore.jks
System property has been set for javax.net.ssl.keyStorePassword with value gDKPNF3pxwOk
Setting up TM service with config /opt/Avaya/JBoss/6.1.0/jboss-as/server/avmgmt/conf/tm/ and service name TM_INBOUND_TLS
System property has been set for javax.net.ssl.trustStore with value /opt/Avaya/JBoss/6.1.0/jboss-as/server/avmgmt/conf/tm//truststore/default_truststore.jks
System property has been set for javax.net.ssl.trustStorePassword with value gDKPNF3pxwOk
tmConfigurationLocation in TMCli is /opt/Avaya/JBoss/6.1.0/jboss-as/server/avmgmt/conf/tm/
****************************
TM Initialization success.
****************************
Return Code: 0 (TM Initialization success.)
Mon Nov 18 17:23:22 GST 2019 : Restarting Postgres service...
Stopping postgresql service: [ OK ]
Waiting for Postmaster PID file creation .
Waiting for Postmaster DB connection availability .
Starting postgresql service: [ OK ]
Mon Nov 18 17:23:26 GST 2019 : Startup of Postgres done
Mon Nov 18 17:24:11 GST 2019 cnd_tls_reconfigurator.sh:32 :: About to reconfigure CND TLS certificates
Mon Nov 18 17:24:15 GST 2019 cnd_tls_reconfigurator.sh:37 :: SUCCESS








